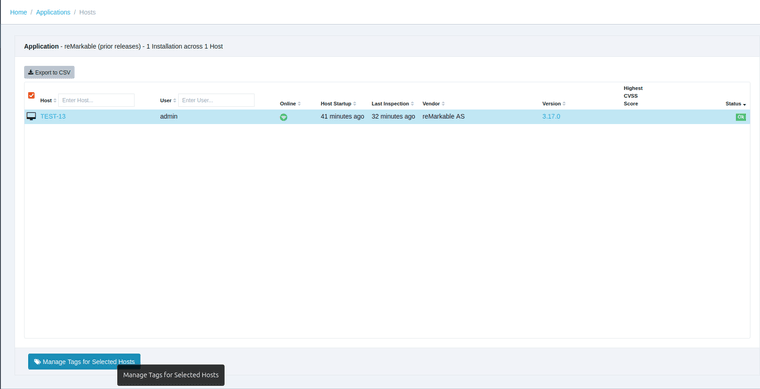
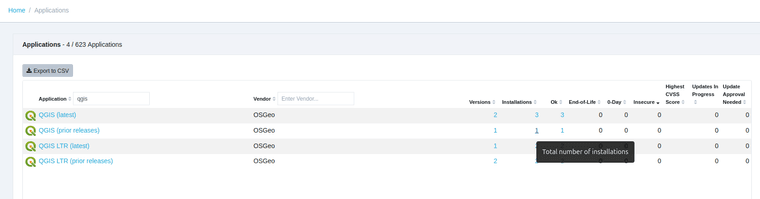
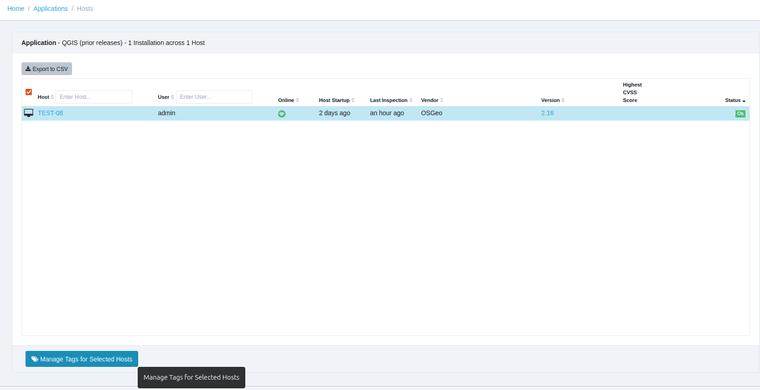
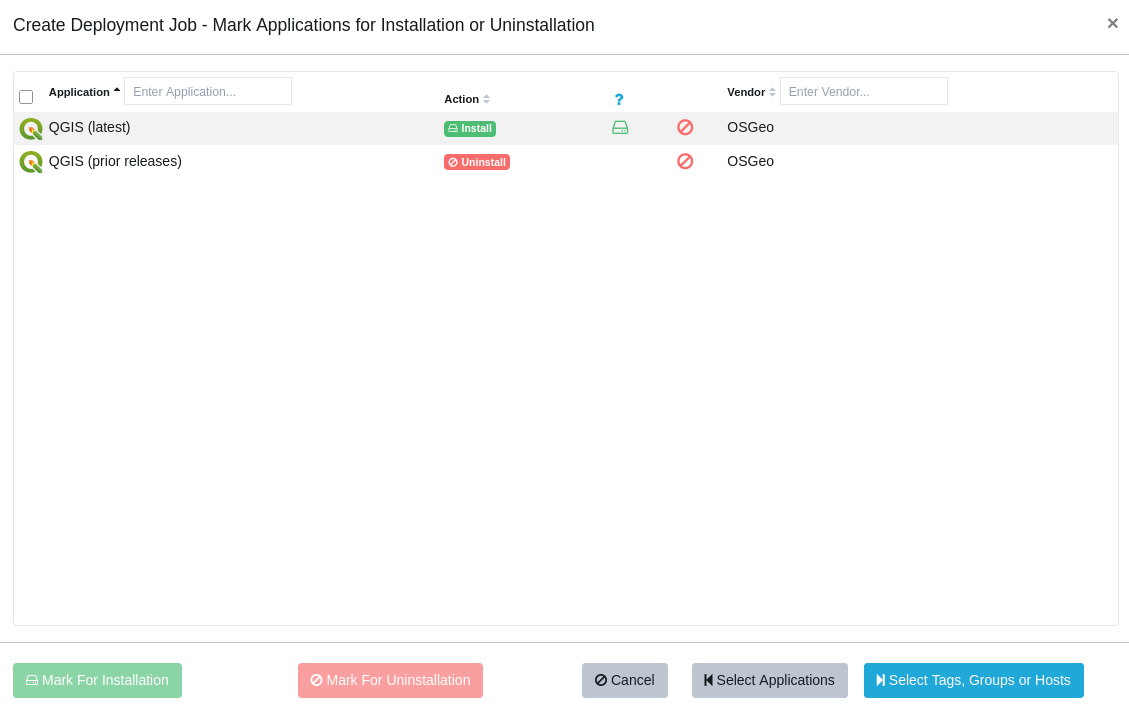
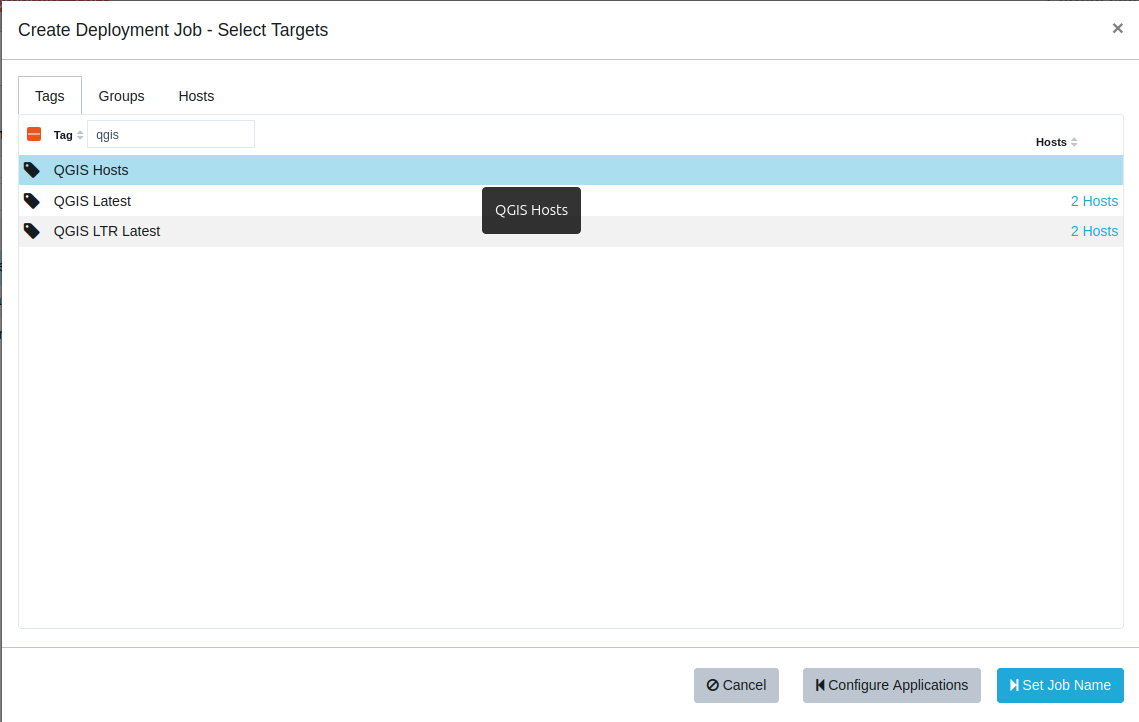
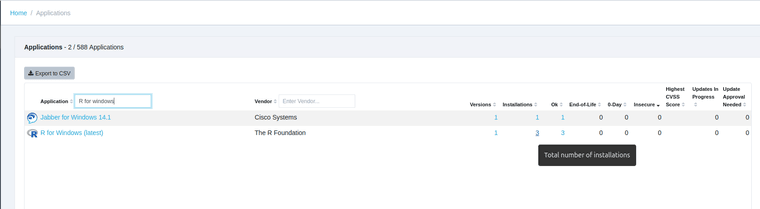
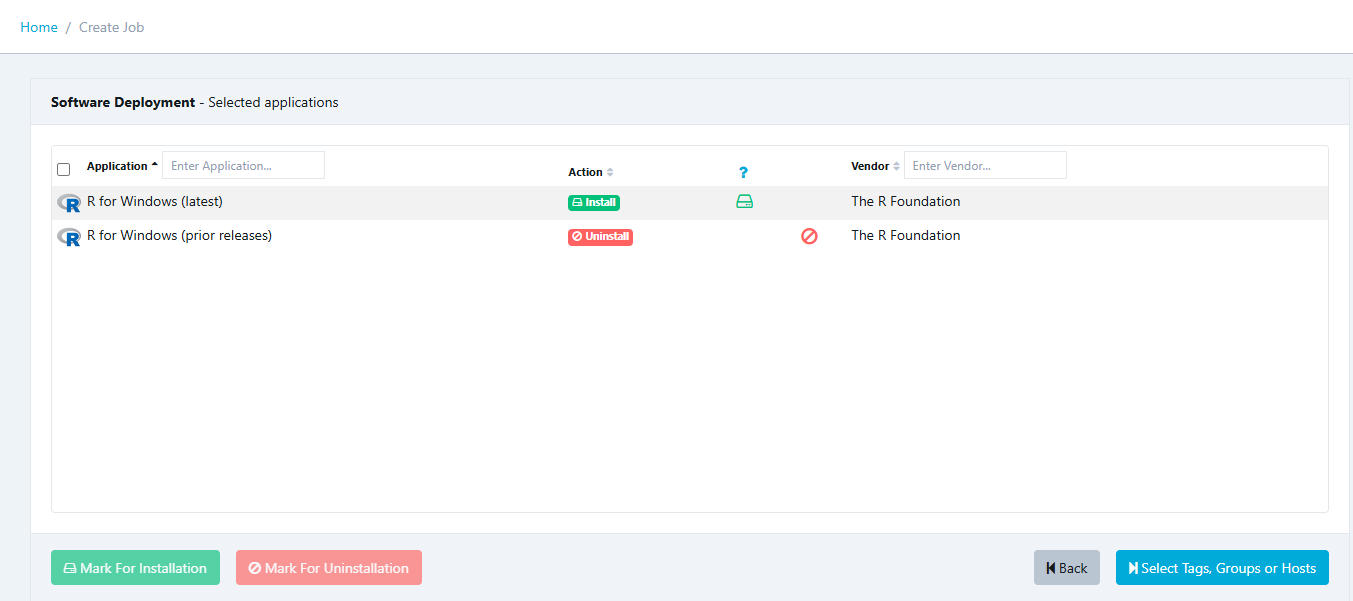
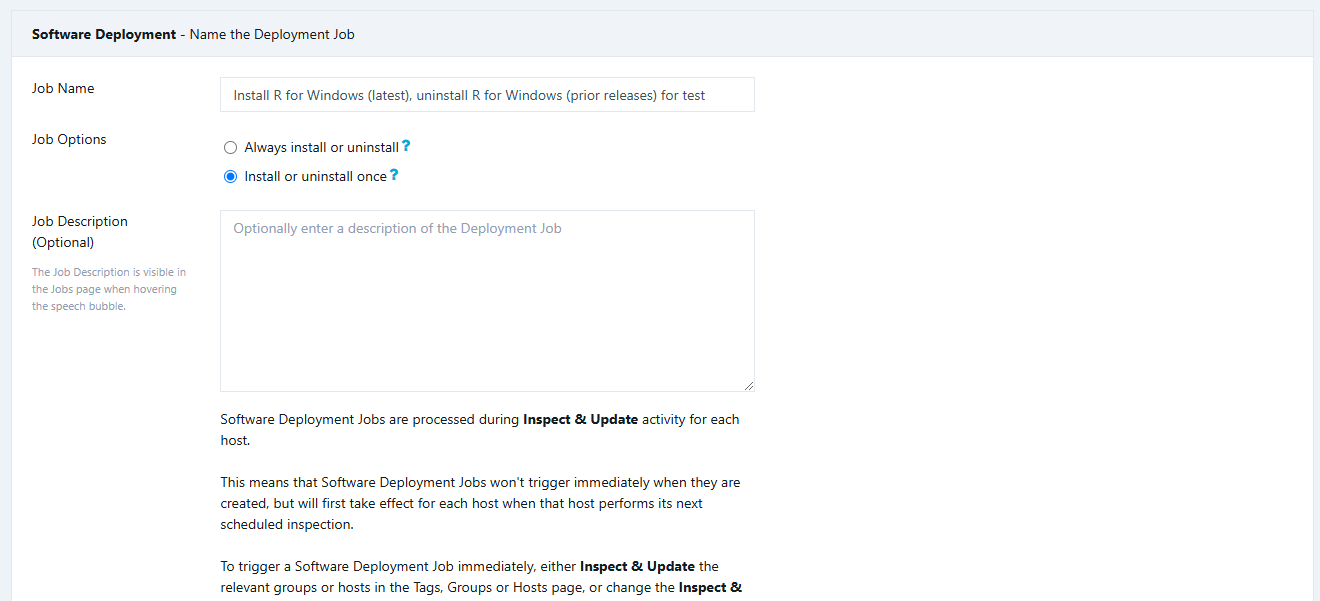
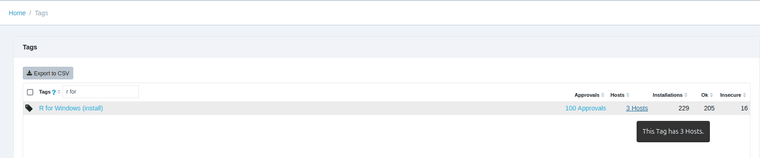
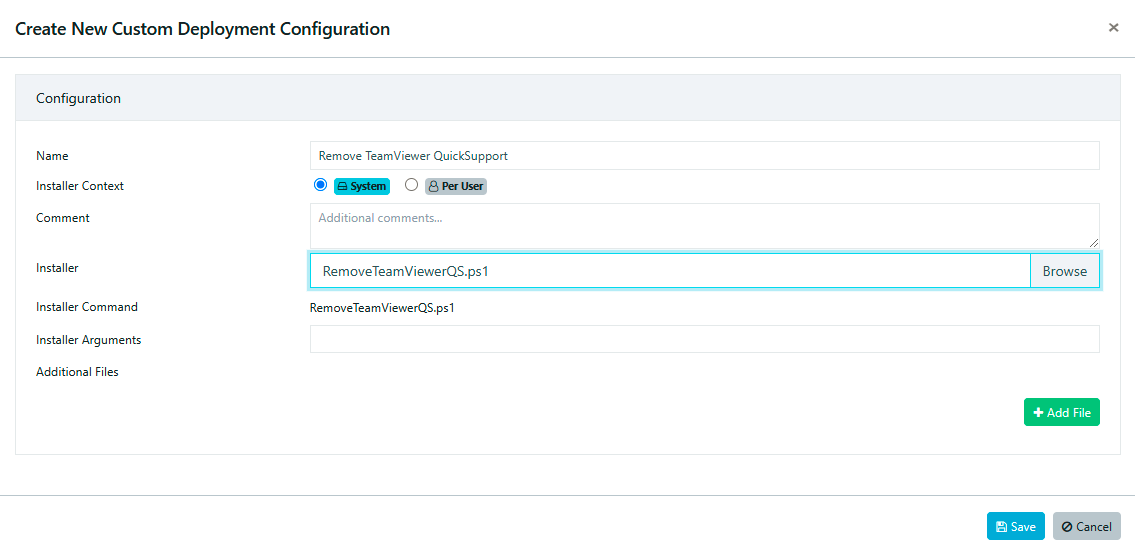
TightVNC can be upgraded using the Custom Software feature in VulnDetect - Corporate:
https://corporate.vulndetect.com/#/deployment/custom-create-job
Download the latest installers from the official website:
https://www.tightvnc.com/download.html
The parameters used in this guide are present in TightVNC's official documentation:
https://www.tightvnc.com/doc/win/TightVNC_2.7_for_Windows_Installing_from_MSI_Packages.pdf
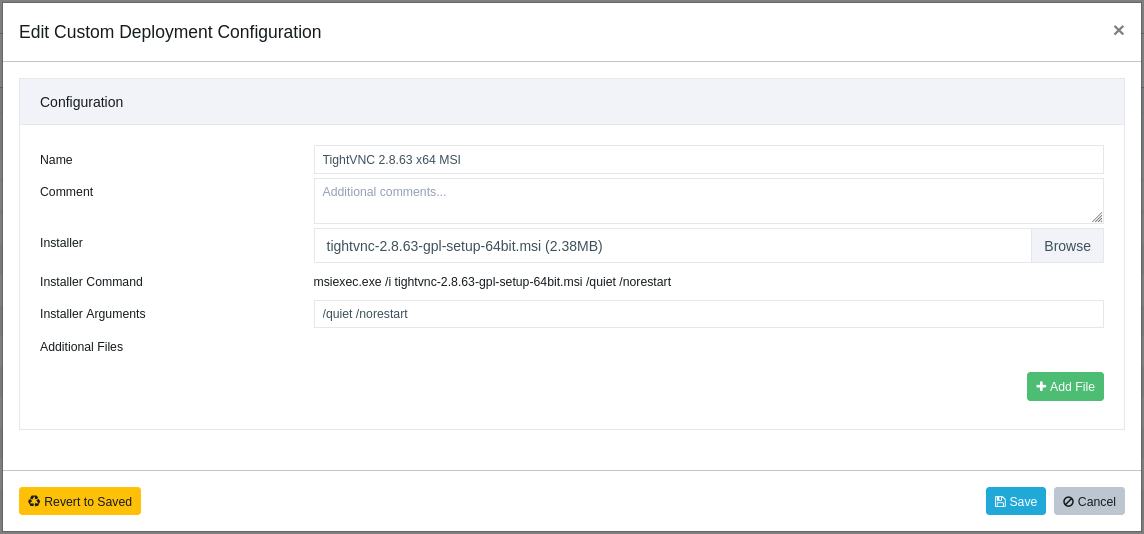
To install TightVNC with its default settings use /quiet /norestart, this will install (or upgrade) both Viewer and Server.
If you would like to install a specific component of TightVNC, use the standard MSI property
named ADDLOCAL. The following three commands install only the server part, only the client part
and both parts, correspondingly:
• msiexec /i tightvnc-2.8.63-gpl-setup-64bit.msi /quiet /norestart ADDLOCAL=Server
• msiexec /i tightvnc-2.8.63-gpl-setup-64bit.msi /quiet /norestart ADDLOCAL=Viewer
• msiexec /i tightvnc-2.8.63-gpl-setup-64bit.msi /quiet /norestart ADDLOCAL="Server,Viewer"
Note that running the installer with e.g., ADDLOCAL=Server, on a system with both Viewer and Server, will remove the Viewer.
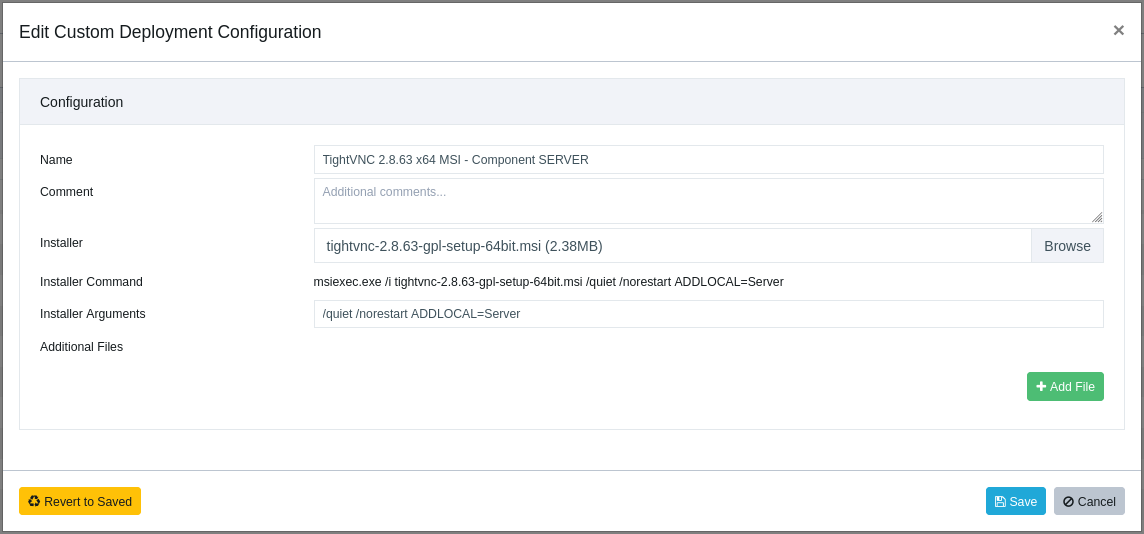
TightVNC with the Server component only.