Custom Software & Advanced Customisation - Technical Usage Guide
These features allow you to deploy Windows installers and supporting files to any Windows device.
Both features work the same way operationally; Advanced Customisation ties into our version-based detection for supported applications.
- What the System Does
Execution Context
Each job runs either as SYSTEM or as the logged-in user.
Advanced Customisation automatically selects the correct context for the target app.
All uploaded files are placed into a temporary working directory controlled by our package wrapper. This directory is cleaned up automatically after execution.
- Primary Installer vs. Additional Files
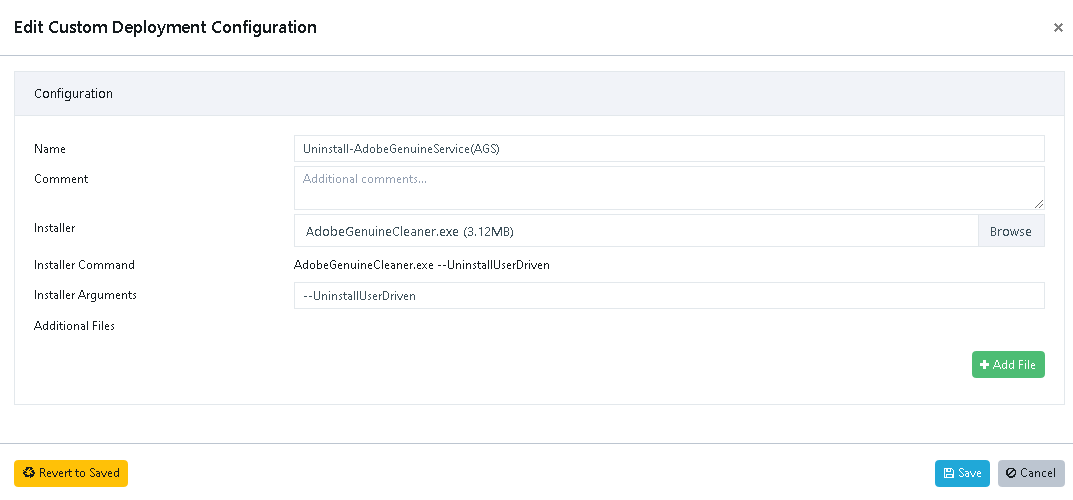
Primary Installer
Only the primary installer is executed.
Supported primary file types:
• .msi
• .msp
• .exe
• .ps1
• .bat
• adobe*.zip (special handling; primary only)
You can supply arguments for the primary installer.
Additional Files
Additional files are placed in the working directory but are not executed automatically.
Typical uses:
• Transforms/configs (.mst, .cfg, .xml)
• Supporting content (.zip, .ini, etc.)
• Registry files (.reg)
If a secondary file must be executed, make the primary file a script and orchestrate everything from there.
Example using .mst:
https://vulndetect.org/topic/2382/foxit-phantompdf-to-foxit-pdf-editor-upgrade
- File-Type Behaviour
MSI / MSP / EXE
Executed using the arguments you provide.
All standard environment variables behave as expected for the chosen context (SYSTEM/user).
Example:
https://vulndetect.org/topic/2540/openvpn-install-upgrade
https://vulndetect.org/topic/2382/foxit-phantompdf-to-foxit-pdf-editor-upgrade
Scripts (.ps1, .bat)
Executed as the primary installer.
Scripts run under PowerShell 5.1 or CMD.
If a restricted PowerShell language mode is enforced, execution will fail.
Example:
https://vulndetect.org/topic/2386/running-powershell-scripts
REG Files (.reg)
Automatically imported using:
reg import filename.reg
No additional processing is performed.
Example:
https://vulndetect.org/topic/2388/registry-files-and-the-custom-software-feature
ZIP Files
General ZIP Files
Extracted automatically into the working directory.
Nothing is executed automatically — your script/installer must make use of the extracted content.
Adobe ZIP Archives (adobe*.zip)
When the primary file matches adobe*.zip, the system will:
1. Extract the archive using 7-Zip
2. Locate the Adobe setup installer
3. Execute it automatically
The ZIP must be the unmodified package downloaded from the Adobe Creative Cloud portal.
Example:
https://vulndetect.org/topic/2385/adobe-creative-cloud-install-upgrade
- Working Directory
All uploaded files — primary and additional — are placed in the same temporary folder.
Relative references such as:
myconfig.xml
.\transform.mst
work normally.
Subfolders are not created unless your installer or script creates them.
Example:
https://vulndetect.org/topic/2621/install-autocad-lt
- Detection & Success Criteria
Custom Software
• Accepted success codes: 0, 3010, 1603
• No version-based detection
• Exit codes only determine whether a reboot is required
Advanced Customisation
• Version-based detection tied to the application’s Recommended Version
• Whitelisted success/reboot codes (varies per app)
• More reliable detection overall
- Common Use Cases
MSI with transform/config
Primary: myapp.msi
Additional: custom.mst, config.xml
Arguments:
msiexec /i myapp.msi TRANSFORMS=custom.mst /qn
Script orchestrating secondary actions
Primary: install.ps1
Additional: payload.zip, settings.reg
The script handles extraction, registry import, and any secondary execution.
Adobe Creative Cloud package
Primary: adobe-designteam.zip
The ZIP is extracted automatically and the internal Adobe setup installer is executed.
Installer requiring bundled resources
Primary: setup.exe
Additional: resources.zip
The ZIP is extracted automatically; your installer must reference the extracted content.
- Operational Notes
• Only the primary installer receives arguments.
• Use a script as the primary file for multi-step processes.
• Execution context provides standard environment variables (similar to Task Scheduler).
• PowerShell 5.1 is always available; restricted modes will break the wrapper.